- Published on
Smart Contract Security Common Vulnerabilities and Solutions
- Authors

- Name
- Adil ABBADI
Introduction
Smart contracts have revolutionized the way we conduct transactions and execute agreements on the blockchain. However, as with any complex system, they are not immune to security vulnerabilities. In this blog post, we will explore common vulnerabilities in smart contracts, their consequences, and most importantly, solutions to prevent them.
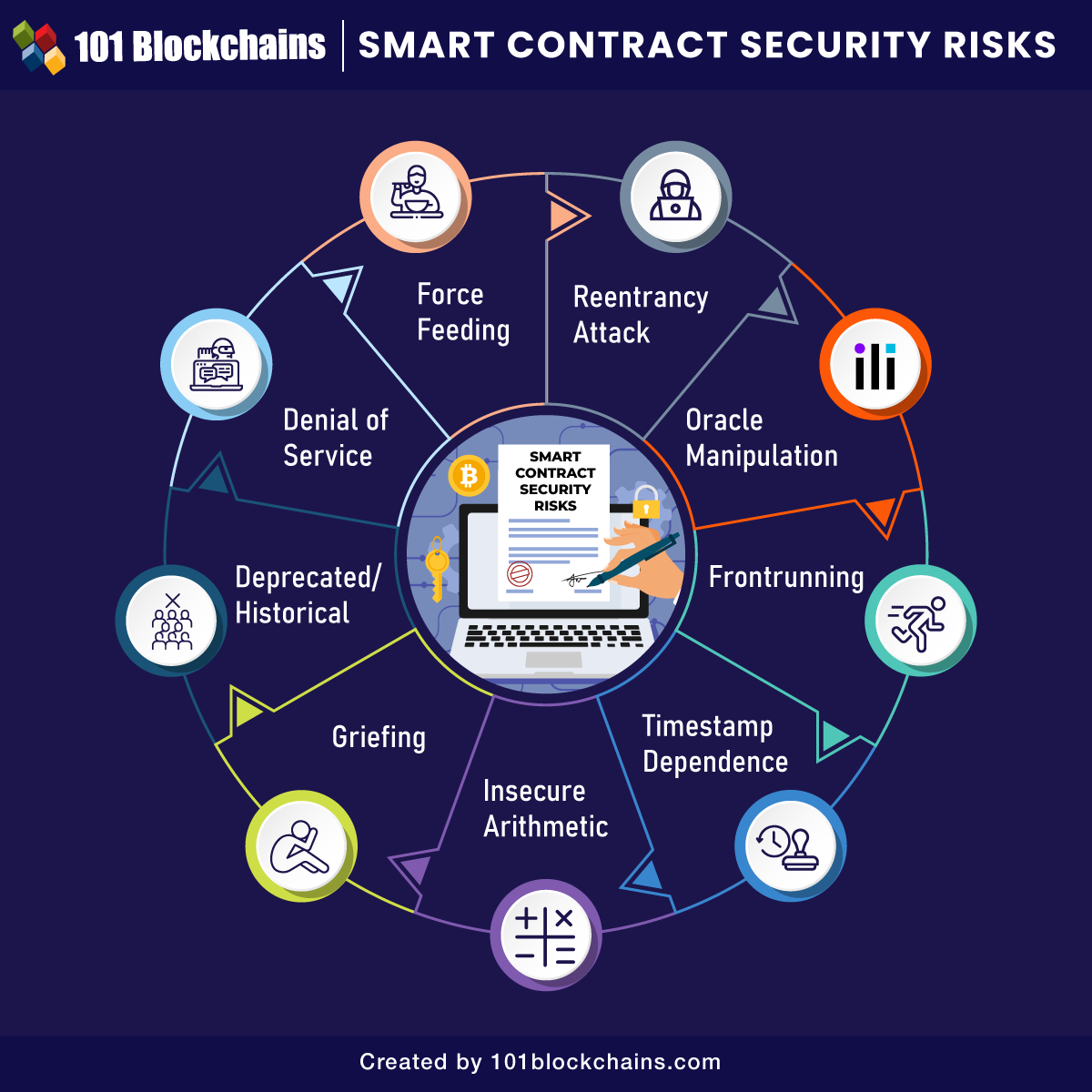
- Common Vulnerabilities in Smart Contracts
- Best Practices for Smart Contract Security
- Conclusion
- Stay Ahead of Smart Contract Security Threats
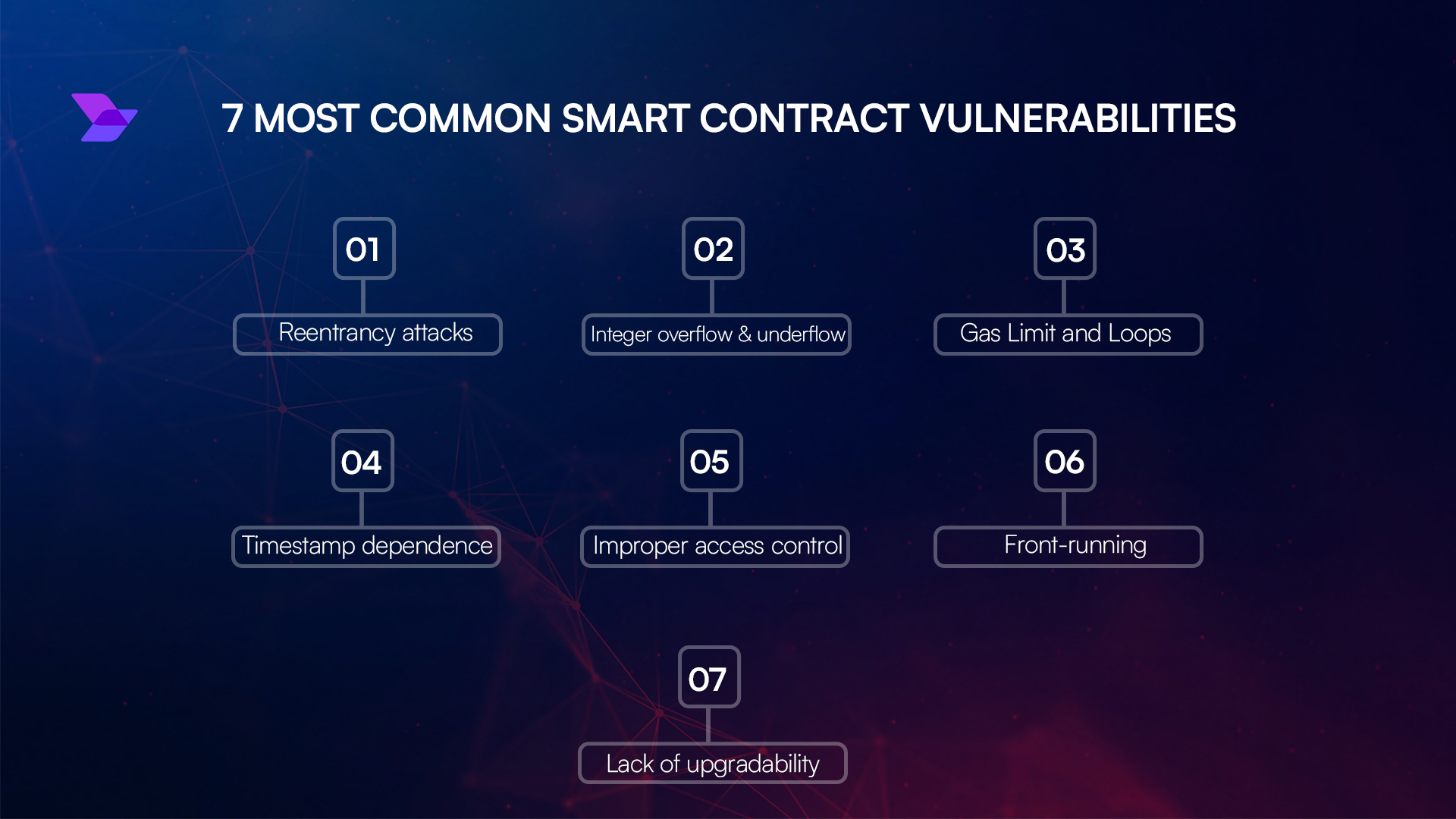
Common Vulnerabilities in Smart Contracts
1. Reentrancy Attacks
Reentrancy attacks occur when a contract calls another contract, which in turn calls the original contract, creating a recursive loop. This can lead to a drain of funds or a contract lockout.
Solution: Use the Checks-Effects-Interactions pattern to separate the verification of conditions from the execution of actions.
2. Unprotected Ether Withdrawal
Leaving ether unsecured in a contract can make it vulnerable to theft.
Solution: Implement proper access control mechanisms, such as multi-sig wallets or timelocks, to restrict unwanted access to ether.
3. Front-Running
Front-running attacks occur when a malicious actor intercepts and modifies a transaction before it is confirmed on the blockchain.
Solution: Implement mechanisms like commit-reveal schemes or hashed time-locked contracts to prevent front-running attacks.
4. Unsecured Use of tx.origin
Using tx.origin to authenticate users can lead to phishing attacks.
Solution: Use msg.sender instead of tx.origin to authenticate users, and implement proper authentication mechanisms.
5. Integer Overflow and Underflow
Integer overflow and underflow can occur when a contract performs arithmetic operations that exceed the maximum or minimum value of an integer.
Solution: Use libraries like Safemath to perform arithmetic operations safely.
6. Unprotected Function Calls
Unprotected function calls can allow unauthorized access to sensitive functions.
Solution: Implement access modifiers, such as public, private, or internal, to restrict access to functions.
7. Out-of-Gas Exceptions
Out-of-gas exceptions can occur when a contract runs out of gas during execution.
Solution: Optimize gas usage by using efficient algorithms, caching, and minimizing the number of external calls.
8. Uninitialized Variables
Uninitialized variables can lead to unexpected behavior or security vulnerabilities.
Solution: Initialize variables properly, and use tools like solhint to detect uninitialized variables.
Best Practices for Smart Contract Security
1. Code Review and Auditing
Perform regular code reviews and audits to identify vulnerabilities and improve code quality.
2. Testing and Simulation
Thoroughly test and simulate smart contract execution to identify potential vulnerabilities.
3. Secure Development Lifecycle
Adopt a secure development lifecycle that includes security considerations at every stage of development.
4. Use of Reputable Libraries and Frameworks
Use reputable libraries and frameworks, such as OpenZeppelin, to ensure that your contracts are built on a secure foundation.
5. Continuous Monitoring
Continuously monitor your smart contracts for suspicious activity and potential security breaches.
6. Bug Bounty Programs
Implement bug bounty programs to incentivize responsible disclosure of security vulnerabilities.
7. Secure Deployment
Deploy smart contracts securely, using mechanisms like multisig wallets and timelocks, to restrict unwanted access.
8. Ongoing Maintenance and Updates
Regularly update and maintain your smart contracts to ensure that they remain secure and up-to-date.
Conclusion
Smart contract security is a critical concern in the blockchain ecosystem. By understanding common vulnerabilities and implementing best practices and solutions, developers can build secure and reliable smart contracts that protect users' assets and ensure the integrity of the blockchain.
Stay Ahead of Smart Contract Security Threats
Stay informed about the latest smart contract security threats and best practices by following industry leaders and security researchers. Remember, a secure smart contract is a reliable smart contract.
Start building secure smart contracts today and ensure a safer blockchain ecosystem for tomorrow.
