- Published on
Post-Quantum Cryptography Beyond ECC
- Authors

- Name
- Adil ABBADI
Introduction
The dawn of quantum computing is upon us, and with it, the threat of quantum attacks on our cryptographic systems. Traditional public-key cryptography, relied upon for secure online transactions and communication, is vulnerable to these attacks. Elliptic Curve Cryptography (ECC), a popular cryptographic technique, is no exception. As the quantum era approaches, it's essential to explore Post-Quantum Cryptography (PQC) and the alternatives to ECC that will safeguard our digital world.
- The Quantum Threat
- Beyond ECC: Post-Quantum Cryptography
- Challenges and Future Directions
- Conclusion
- Further Reading and Exploration
The Quantum Threat
Classical computers use bits to process information, whereas quantum computers employ qubits (quantum bits). This fundamental difference allows quantum computers to perform certain calculations exponentially faster than their classical counterparts. In the context of cryptography, this means that a large-scale quantum computer could potentially break many encryption algorithms currently in use, including ECC.
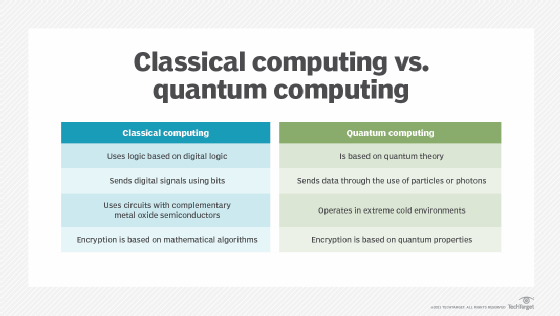
Beyond ECC: Post-Quantum Cryptography
Post-Quantum Cryptography focuses on developing cryptographic algorithms resistant to quantum attacks. While ECC is widely used, its quantum vulnerability has prompted the exploration of alternative cryptographic techniques. Some prominent Post-Quantum Cryptography candidates include:
1. Lattice-Based Cryptography
Lattice-based cryptography relies on the hardness of problems related to lattices, a mathematical concept. The most popular lattice-based scheme is the NTRU cryptosystem. NTRU is based on the shortest vector problem (SVP) and the learning with errors (LWE) problem, making it resistant to quantum attacks.
def ntru_encrypt(plaintext, public_key):
# NTRU encryption implementation
return encrypted_text
2. Code-Based Cryptography
Code-based cryptography uses error-correcting codes to construct cryptographic primitives. The McEliece cryptosystem is a popular example, relying on the hardness of the decoding problem for a certain class of codes.
def mceliece_encrypt(plaintext, public_key):
# McEliece encryption implementation
return encrypted_text

3. Multivariate Cryptography
Multivariate cryptography is based on the hardness of problems related to multivariate polynomials. The Rainbow and SIDH schemes are examples of multivariate cryptography. These schemes are often more efficient than lattice-based and code-based cryptography but are still in the early stages of development.
def rainbow_encrypt(plaintext, public_key):
# Rainbow encryption implementation
return encrypted_text

4. Hash-Based Signatures
Hash-based signatures, such as the SPHINCS scheme, are a type of digital signature. These signatures are based on the hardness of problems related to hash functions and are quantum-resistant. Hash-based signatures are often more efficient than other Post-Quantum Cryptography schemes.
def sphincs_sign(message, private_key):
# SPHINCS signature implementation
return signature
Challenges and Future Directions
While Post-Quantum Cryptography offers a promising solution to the quantum threat, several challenges remain:
- Performance: Post-Quantum Cryptography schemes often come with increased computational overhead and larger key sizes, affecting performance.
- Implementation: Implementing Post-Quantum Cryptography schemes securely and efficiently is a complex task.
- Standardization: Standardizing Post-Quantum Cryptography schemes is an ongoing effort, with organizations like NIST leading the charge.
Despite these challenges, the Post-Quantum Cryptography community continues to advance, driven by the urgent need for quantum-resistant cryptography.
Conclusion
As we venture into the post-quantum era, it's essential to explore alternatives to ECC and traditional public-key cryptography. Post-Quantum Cryptography offers a range of solutions, each with its unique strengths and weaknesses. By understanding the principles and challenges of Post-Quantum Cryptography, we can ensure a secure digital future, resilient to the threats of quantum computing.
Further Reading and Exploration
- National Institute of Standards and Technology (NIST) Post-Quantum Cryptography Standardization Process
- Post-Quantum Cryptography for Everybody
- Quantum Computing and Post-Quantum Cryptography: A Beginner's Guide
